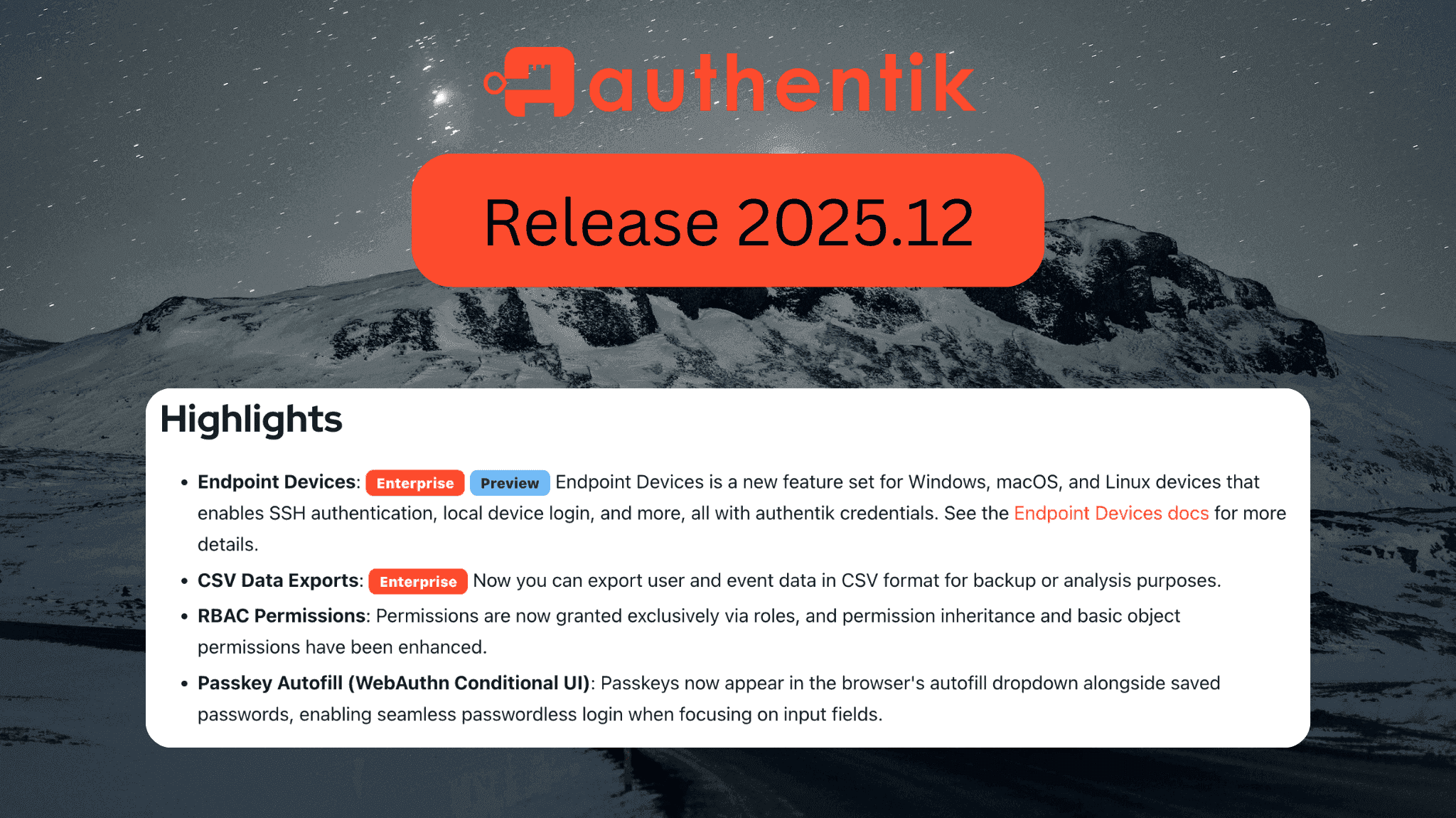
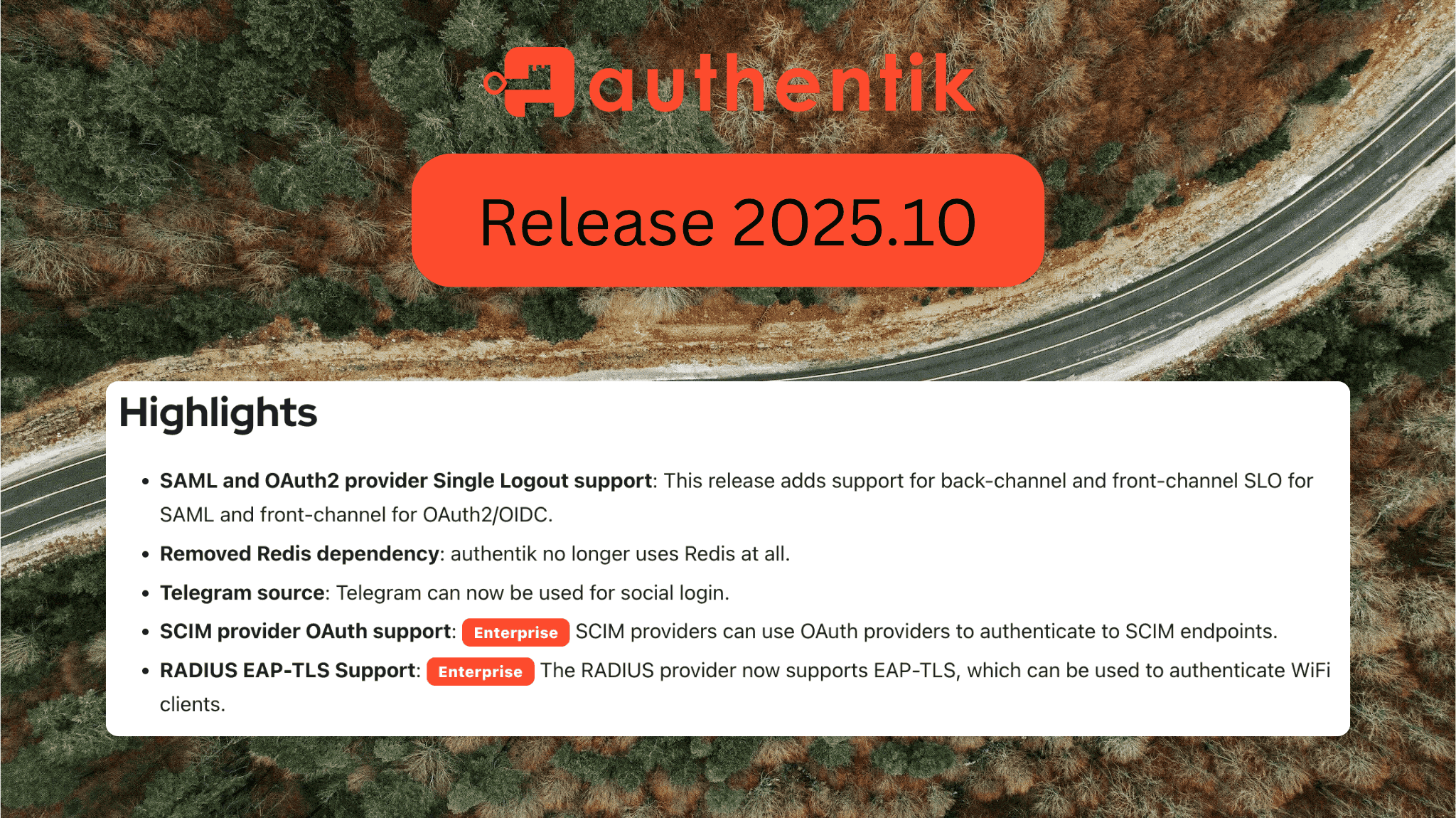
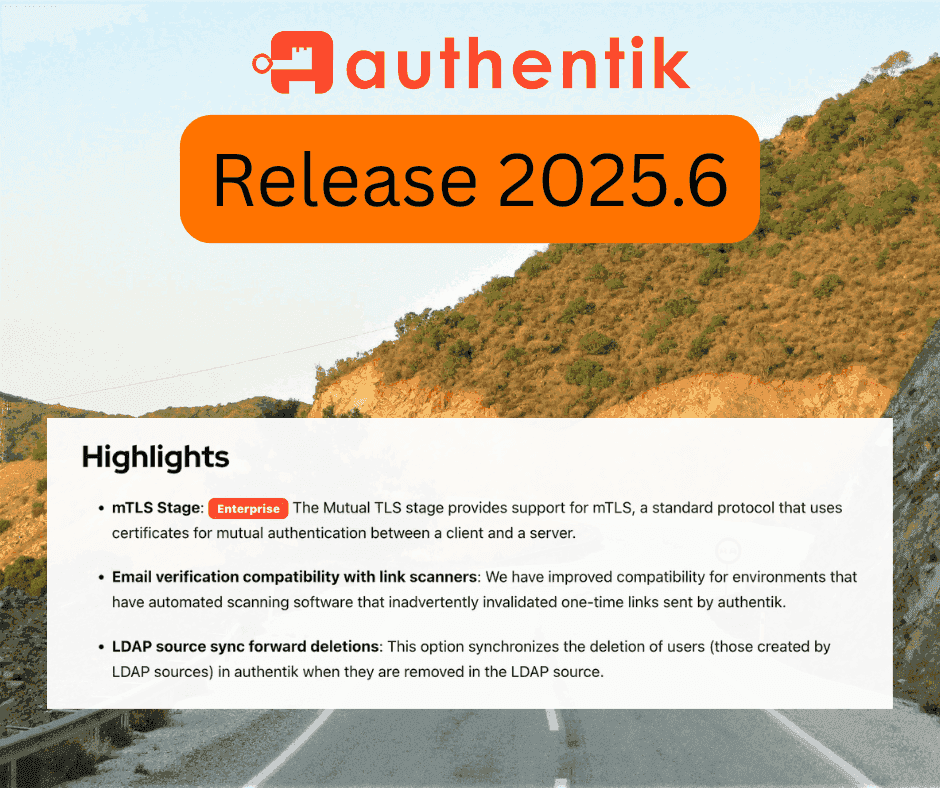
Extended Identity and Access Management with authentik
We are excited to share our vision for Extended Identity and Access Management - XIAM - as authentik expands our ability to secure IAM across all users, devices, and resources, flexibly and resiliently.
I genuinely apologize for releasing yet another acronym on the security world, but this is what we've been steadily building toward for the past seven years, and frankly, none of the current approaches encompasses the breadth and depth of how identity and access management should look like.
With a nod to 1Password for being the first (I think) to mention "XAM" - Extended Access Management - we see a world in which Identity and Access Management are seamlessly managed and supported for everyone, everywhere - extending far beyond what any legacy identity provider or device management system can provide today.
Concretely, XIAM means having one identity and access system for:
- all users (human and non-human; workforce and customer)
- all devices and endpoints (any OS, passkeys, passwordless, biometrics, ...)
- all applications and resources (even legacy apps and remote systems)
- the full user lifecycle (seamless on/offboarding, self-service, management controls)
- running everywhere, resiliently (multi-region, multi-cloud, on-prem)
Let's dive into each of these in more detail: