Release 2024.4 is here: new functionality for Admins, devs, and end users
authentik is an open source Identity Provider that unifies your identity needs into a single platform, replacing Okta, Keycloak, and Ping. Authentik Security is a public benefit company building on top of the open source authentik project.
We are happy to announce that 2024 is going great, with our second release of the year adding important new functionality for Admins, developers, and end users. Take a look at the new features included in the release, check out the Release Notes for more details and upgrade instructions, and enjoy the new features!
We are excited that this release, like our 2024.2 one, continues to add more functionality across the board for all users. For Admins, we added new abilities to verify user credentials and provision users and groups via external IdP sources, additional powerful configuration options, and performance improvements for important API endpoints (User, Groups, Events). For developers, we added an API Client for Python. We also made further UX/usability and customization enhancements, with a revamped UI for log messages and converting several multi-select boxes into dual-select. Using dual-select components across the interface is the goal; they provide a much cleaner UX for our users.
Let’s take a look at some of the highlights of this release.
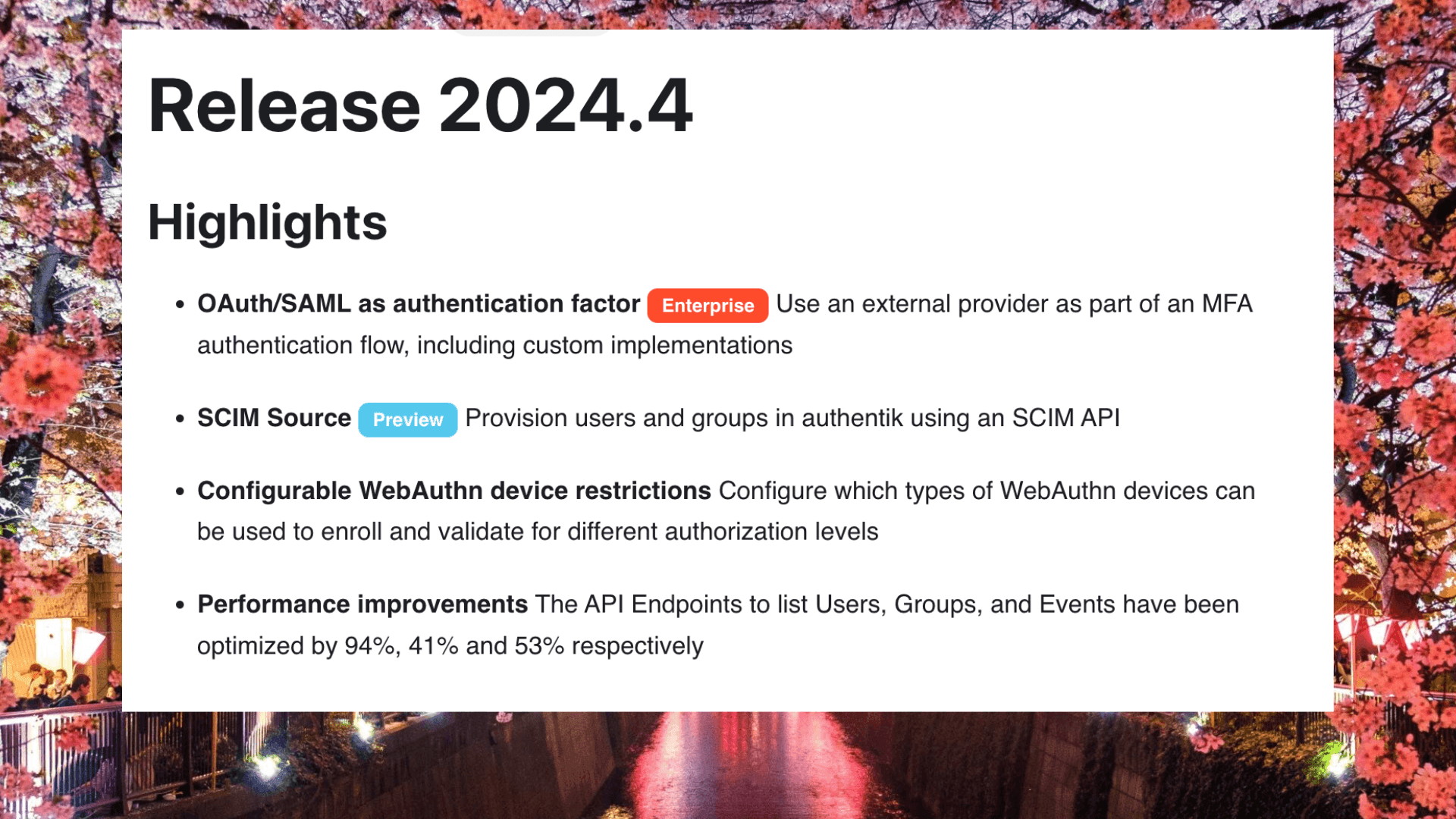
Highlights of the authentik 2024.4 release
- A new Source stage for OAuth or SAML allows for additional, dynamic user verification from external IdP sources.
- A new SCIM Source means that Admins can now provision users and groups in authentik using an SCIM API.
- Configurable WebAuthn device restrictions allows Admins to define which types of WebAuthn devices can be used to enroll and validate for different authorization levels.
- Performance improvements for important API endpoints (User, Groups, Events), optimized by 94%, 41% and 53% respectively.
And there's more...
Python API Client
There's now an official API Client for Python: https://pypi.org/project/authentik-client/. This API Client can be used to create/update/delete objects within authentik as well as using the Flow executor to authenticate.
Configure LDAP sources to not store hashed password in authentik
When authentik is configured to federate with an LDAP source, upon authentication, authentik hashed the password and stored it in its own database. This allows authentication to function when LDAP is unreachable. Admins can now configure this behavior on the LDAP Source configuration page, by toggling off the Update internal password on login option to disable this behavior when it is not wanted.
For details refer to our LDAP Source documentation.
Configurable app password token expiring
Admins can now configure the default token duration (which defaults to minutes=30) in the Admin interface. This value can also be overridden per user with the goauthentik.io/user/token-maximum-lifetime attribute.
Thanks @jmdilly for contributing this feature!
Breaking change
As part of our work to move configuration tasks to our UI (we want to minimize your context switches!) we have removed the following config option from the config file; you can now set this option in either the Admin interface (under System -> Settings) or in the API:
AUTHENTIK_DEFAULT_TOKEN_LENGTH
Note that when upgrading to 2024.4, the currently configured options will be automatically migrated to the database, and can be removed from the .env or Helm values file afterwards.
Happy upgrading and authenticating!
There are even more capabilities and enhancements beyond what we covered here in this post, so be sure to read the Release Notes for version 2024.4, and as always, let us know your thoughts.
