Identity: Self-hosted or in the cloud?
authentik is an open source Identity Provider that unifies your identity needs into a single platform, replacing Okta, Keycloak, and Ping. Authentik Security is a public benefit company building on top of the open source authentik project.
In October 2023, Cloudflare announced that they had discovered yet another Okta compromise.
Cloudflare had to warn Okta first and show them how they had been breached via an insecure setup with a third-party service provider. A leading company offering security and identity as a service instead introduced insecurity.
Over the past decade or so, SaaS has become the dominant model for delivering software, and yet, such incidents aren’t surprising. The SaaS business model was supposed to align vendor and customer interests, while the technology allowed rapid updates and improvements. SaaS was supposed to bring an end to throwing software over the wall and letting customers deal with it.
Recently, however, we’ve seen many companies fleeing SaaS providers to build private clouds and run self-hosted software. At Authentik Security, we have seen more and more customers canceling legacy SaaS providers to take back control of their identity needs with our self-hosted solution.
At first glance, it looks like people are going back in time, but self-hosted software has advanced despite the popularity of SaaS and is increasingly likely to beat SaaS options across numerous measures. In this post, I’ll walk through why the industry defaults have changed and why we believe in focusing on a self-hosted product.
20 years in, and the end of software is nowhere in sight
More than two decades ago, Marc Benioff, CEO and founder of Salesforce, debuted a marketing campaign focused on convincing IT leaders that all software would end up in the cloud and be delivered through the browser and via SaaS models.
This prediction was overambitious, and we’re starting to see the rise of modernized self-hosted businesses that can compete with SaaS providers. To better understand the re-emergence of self-hosting, let’s reexamine those predictions and see how they failed.
Does SaaS actually align vendor and customer success?
It’s right in the name – software as a service instead of software as a product. Theoretically, the incentives for SaaS providers should be better aligned with users than those of ship-it-and-forget-it software providers. Or, that was the idea.
In reality, SaaS companies have numerous incentives to work against the interests of their users. SaaS companies are liable to increase their prices with little warning (such as Evernote, which suddenly doubled its prices), implement an SSO tax that makes it expensive to take basic security measures, and refuse to communicate to customers about outages (such as Atlassian, which didn’t acknowledge a 2022 outage for nine days, even though it affected close to 400 companies and as many as 800,000 users).
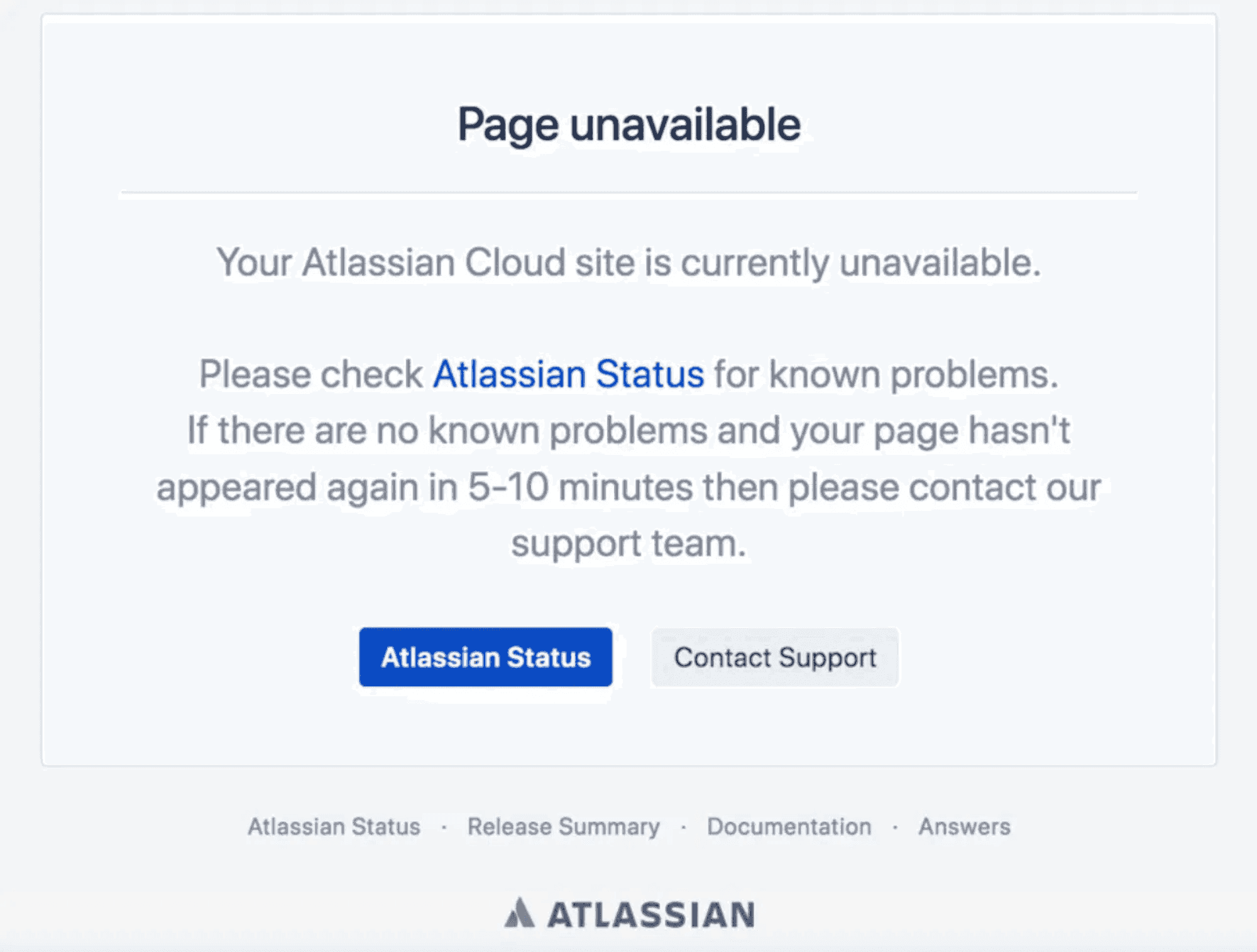
You’d at least think that the alignment would be stronger in security industries, but the opposite proves true. Okta, for example, obscured the news about a data breach instead of proactively warning its customers. Okta itself admits this isn’t just a one-off problem:
In November 2023, Okta co-founder Todd McKinnon said, “Our focus was enabling technology and making it easy to adopt the cloud. It wasn't necessarily started 15 years ago as a cyber[security] company. […] It's kind of clear to everyone that we're short of where we need to be now.”
The incentives the SaaS model purports to offer are clearly not as strong as the industry once thought. Self-hosted products, in contrast, can offer more straightforward and predictable pricing since the business model doesn’t depend on such a wide range of customers depending on one-size-fits-all infrastructure.
Customers only pay for what they use, and the costs are predictable given the control they have over their own infrastructure, whereas with legacy SaaS, customers are eventually stuck footing the bill for a SaaS provider’s infrastructure always needing to grow more sprawling and complex.
Is SaaS software actually easier to use, install, and upgrade?
Initially, the switch from heavy-duty self-hosted software to SaaS felt like magic. When SaaS first emerged, self-hosted providers hadn’t done much to make the installation and upgrade processes easy. It made sense for SaaS proponents to predict that SaaS software would always be easier to manage.
In reality, we’ve seen this isn’t as true as they thought. With the rise of IaaS, CI/CD, and configuration management tools – more particularly, Docker and Kubernetes – modern self-hosted software is very easy to adopt, manage, and maintain. As DHH writes, “Up until very recently, everyone ran their own servers, and much of the progress in tooling that enabled the cloud is available for your own machines as well.”
In the past, self-hosted identity solutions like Microsoft ADFS were unwieldy, which gave companies like Okta and Auth0 their original market opportunities, but self-hosted products (and their surrounding infrastructure) have since caught up.
Now, when most of a company’s infrastructure already runs on a private cloud with cloud-native tooling, it’s actually easier to run containerized self-hosted products that can tie directly and securely into this existing infrastructure. Counter to the original promise of SaaS, it’s now more difficult to plug an external SaaS provider into existing infrastructure and ensure it integrates and synchronizes sensitive data.
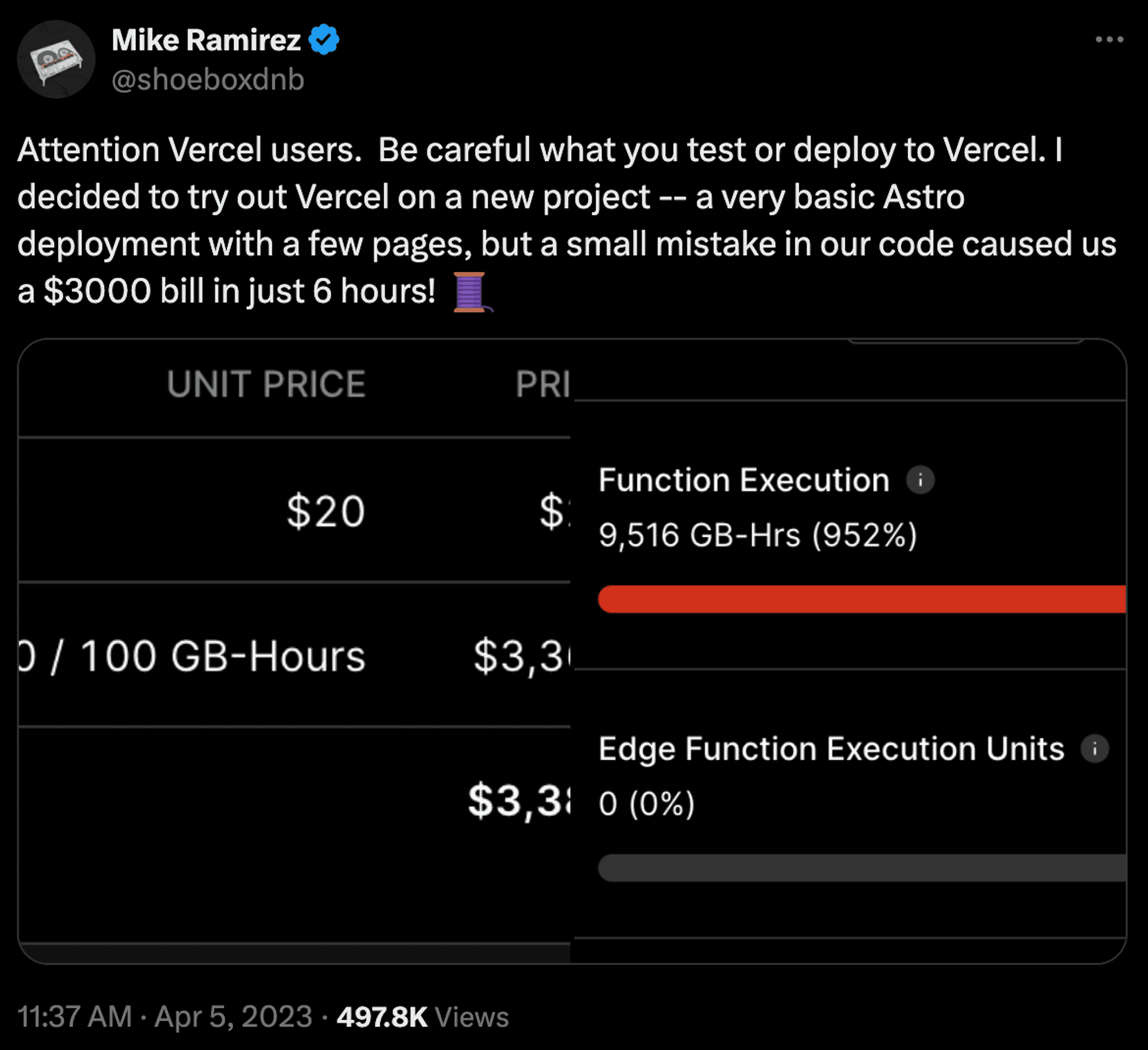
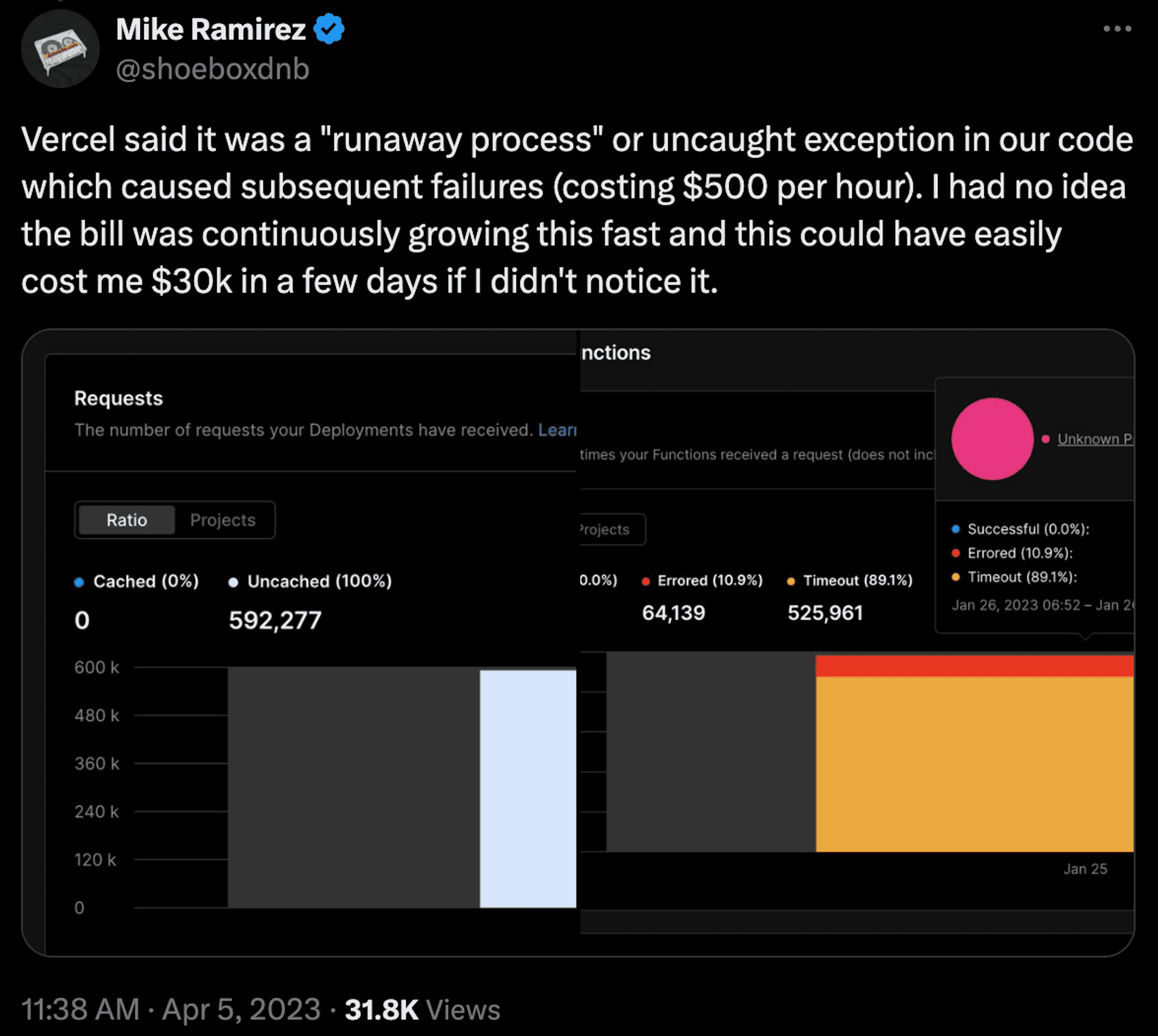
Cloud services, in general, have come under a lot of scrutiny for being hard to manage. There are now entire services dedicated to helping companies monitor their cloud usage and consultancies focused entirely on lowering runaway cloud costs.
Are SaaS providers actually better for critical infrastructure than self-hosted options?
If we could go back in time and share these realities with the SaaS advocates of ten years ago, I think they’d be surprised, but they’d also accept that SaaS would have tradeoffs. They’d likely insist, though, that SaaS would keep a firm hold on critical infrastructure.
Reality has shown that self-hosted environments can be just as reliable and secure as SaaS providers, if not more so.
By working with a SaaS provider (and, in practice, many SaaS providers), companies have to increase the surface area of attack their products are vulnerable to. The simple act of sharing sensitive data over the public internet increases your attack surface, and if the vendor shares infrastructure across all of its customers, that spread increases your attack surface even further.
That’s partially why we’ve seen such a steep rise in repeated, massive breaches despite the size of the targets in question.
In reality, it’s much easier to lock down access to sensitive data via one individual organization than doing so via one-size-fits-all SaaS providers trying (and repeatedly failing) to secure every possible customer configuration on shared infrastructure.
A similar pattern applies to reliability. In theory, a SaaS provider should automatically scale with usage, and few customers should deal with disruptions. In reality, when a SaaS provider suffers service disruptions, customers have to wait and hope to regain availability.
Service disruptions also tend to be more likely because SaaS providers necessarily have massively complex infrastructures. Because SaaS promises to be one size fits all, SaaS providers need to build infrastructures that can serve all of their customers at once, even though usage patterns can vary widely among their customers. As a result, SaaS systems have to get complex, and complex systems are intrinsically hazardous.
In contrast, self-hosted software can be more easily configured for high availability and redundancy, providing automated failover mechanisms and reliability at any scale. Of course, most cloud providers guarantee a minimum level of uptime – often 99.99% – but “uptime” doesn’t always reflect a customer’s desired experience.
Okta, for example, has a history of service degradation issues that Okta doesn’t count against its total uptime (as do many other SaaS providers). And even in an “ideal” 99.99% world, customers would still end up with core services unavailable for nearly an hour every year. With identity, that could leave employees with no access to everything they need to get work done, and customers stuck waiting for a fix from the SaaS vendor.
Three reasons to consider self-hosting
Don’t take us as contrarians. The pendulum isn’t just swinging fully back from SaaS to self-hosted. Instead, I predict we’ll see companies in particular industries and with particular use cases adopt self-hosted models as they weigh changing criteria against reality.
In particular, we’ll see companies that care a lot about data privacy, reliability, and flexibility shift toward self-hosted software for security-critical services.
1. Data privacy
With self-hosted software, companies can build their infrastructure around stricter, narrower security needs than SaaS providers can offer. For some, this will be the biggest reason to switch, while for others, this reason alone will be enough.
By self-hosting software, you can run it behind your own firewall and keep all critical data in-house. You don’t even need an Internet connection to access this data.
This level of control and privacy is especially important for companies that must comply with privacy and compliance regulations such as GDPR or FedRAMP requirements. Companies can opt for self-hosted just to defray risk (especially given the possibility of being fined for an issue on the SaaS provider’s side).
Authentik Security’s customers, for example, include companies that can’t send data over the public internet for compliance reasons and companies that can’t always rely on the internet's availability.
2. Reliability
With self-hosted software, companies can determine the level of reliability and scalability they want, have full control over fulfilling those requirements, and pay only for what they use.
37Signals provides a good example of this in action. When the company moved out of the cloud and onto bare metal, many predicted a lack of reliability would be their biggest regret. In reality, DHH writes the cloud is a better fit only for brand-new companies that want to get started quickly and for large companies with very irregular loads.
“Neither of those two conditions apply to us today,” he writes. “By continuing to operate in the cloud, we're paying an at times almost absurd premium for the possibility that it could. It's like paying a quarter of your house's value for earthquake insurance when you don't live anywhere near a fault line.”
Having to pay for resources you don’t really need is only the beginning of cloud and SaaS costs.
Managing cloud costs is notoriously difficult (and cloud providers don’t have much reason to make it easier), and runaway costs across SaaS providers and cloud middleware are common.
3. Control
The biggest advantage and disadvantage of a SaaS provider are the same: You don’t have to (or get to) have as much control. For some companies, this tradeoff is worthwhile. For others, particularly those with security concerns, the tradeoff comes with tremendous costs.
Theoretically, you’re trading control for simplicity, but even that aspect rarely works in practice. Self-hosting skeptics tend to assume that self-hosted software takes too much time and effort to stand up, maintain, and integrate. In reality, core infrastructure, provided as a service, will inevitably require much more integration work than that.
SaaS solutions, because they try to be one-size-fits-all, tend to be inflexible and non-customizable. Up front, that means a lot of work integrating a SaaS product with the rest of a company’s infrastructure. Over time, that means irregular bursts of maintenance work as the SaaS provider changes the product.
If the SaaS product is a productivity app, this might not matter much. But if the software is core to general operations, like it is with identity management and security, then chasing after your SaaS provider can turn the control and simplicity tradeoff upside down – giving you neither.
Many companies end up with the worst of both worlds: a SaaS provider that promises to be one size fits all but takes away control while removing little complexity. With self-hosted products, in contrast, companies can run software via private cloud or on-prem environments using the same tools and technologies they would have wanted to use anyway.
The future of identity is close to home
Identity access management as a service (IAMaaS) promised to be cheap, flexible, scalable, and, above all, secure.
In reality, customers have received unpredictable costs, rigid products, unreliability, and, worst of all, security products that are fundamentally insecure and opaque.
With the rise of AI-enabled attackers, the continued popularity of remote work and bringing your own devices to work, the spread of applications, and the parallel growth in expenses and breaches, the identity market is at a major fork in the road.
When Cloudflare had to investigate a security incident on Okta’s behalf, many saw it as embarrassing and ironic. When they had to do it again, companies started seeing the cracks in the foundation.
We can’t switch from one SaaS to another over and over again. We need to self-host identity and maintain control over our own futures.
We are interested to hear your thoughts on this topic. Leave some comments here, find us on Discord, or send us an email to [email protected].
Nick Moore contributed to this post.