Announcing Release 2024.10
authentik is an open source Identity Provider that unifies your identity needs into a single platform, replacing Okta, Keycloak, and Ping. Authentik Security is a public benefit company building on top of the open source authentik project.
We are happy to announce that our 2024.10 release is ready, and it’s full of great new features and functionality. This release showcases a good balance of additional security hardening and improved usability with faster, smoother workflows.
Every Identity provider and SSO product should be constantly increasing the security and robustness of the code base and new features, and we think it is also important to continuously and explicitly look for ways to enhance our users’ experience and efficiency.
Release 2024.10 includes these major security features: Chrome Device Trust support, JSON Web Encryption, and enhanced CAPTCHA processing. Further highlights of the release include the ability to configure auto-selected 2FA devices, a new task-based structure for our Tech Docs, and a new highly customizable Invalidation flow that can be configured to prompt with multiple logout and redirect options.
This release highlights our commitment to delivering flexibility, security, and optimal user experience in every version of authentik. Take a look at the Release Notes for more details, and read on to learn more about the new features.
New features and functionality in release 2024.10
-
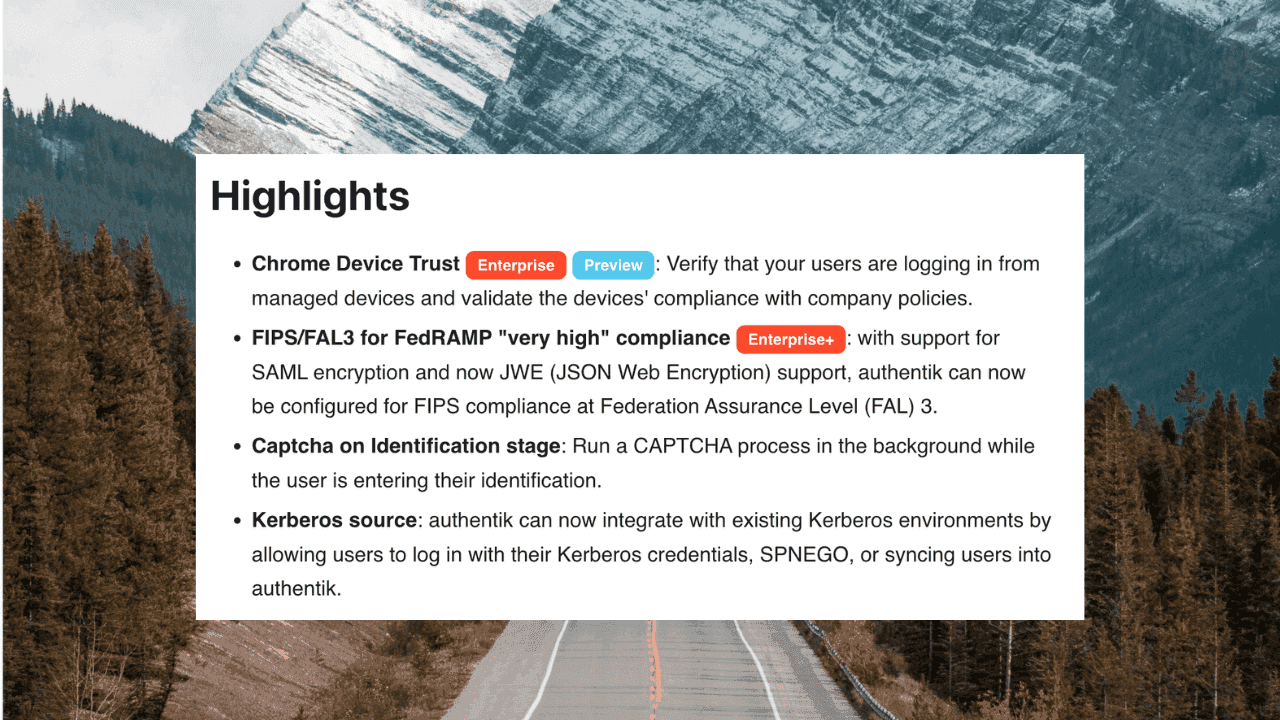
Chrome Device Trust (Enterprise Preview): This is a new stage for Enterprise clients that verifies the user through the Chrome Verified Access API. This stage only works with Google Chrome. You'll need to bring your own Verified Access API instance via Google Cloud. When configured in authentik, this stage means that on any computer or device that has been identified as trusted, you no longer need to enter a verification code each time you sign in.
-
JWE support for OAuth: You can now configure JSON Web Encryption with the OAuth 2.0 Provider, which will encrypt all the tokens created by authentik, using the configured encryption key.
-
FIPS/FAL3 for FedRAMP "very high" compliance (Enterprise+): With support for SAML encryption and now JWE (JSON Web Encryption) support, authentik can now be configured for FIPS compliance at Federation Assurance Level (FAL) 3.
-
Captcha on identification stage: We've added an optional Captcha stage baked into an Identification stage to run in the background while the user inputs their information. Using this should result in lower total time per flow for the end user.
-
Kerberos source: authentik can now integrate with existing Kerberos environments by allowing users to log in with their Kerberos credentials, SPNEGO, or syncing users into authentik.
-
Invalidation flows for providers: The sign-out experience when the session in an application ends can now be configured. Previously where this was always a static page, an invalidation flow can be used now to create a custom logout panel. This can be used for additional validation, or redirecting the user to a custom URL.
-
Auto-select 2FA device: Users who configure multiple 2FA devices will now land on their last used device's prompt, skipping the device picker. This should result in lower total average time per flow for the end user.
-
New structure for authentik's technical documentation: We've restructured the technical documentation in authentik to be more task-based, with sections, titles, and headings that follow the workflow of installing, configuring, and using the product. Previously, our docs were organized by components. This new focus on tasks increases findability within the Table of Contents, and provides a high-level guide of the typical workflows with authentik.
Upgrade to version 2024.10
Refer to our Upgrade documentation and the Release Notes for detailed instructions.
Enjoy the new release, and as always, reach out to us with any questions or feedback! Connect with us on GitHub, Discord, or with an email to [email protected].
