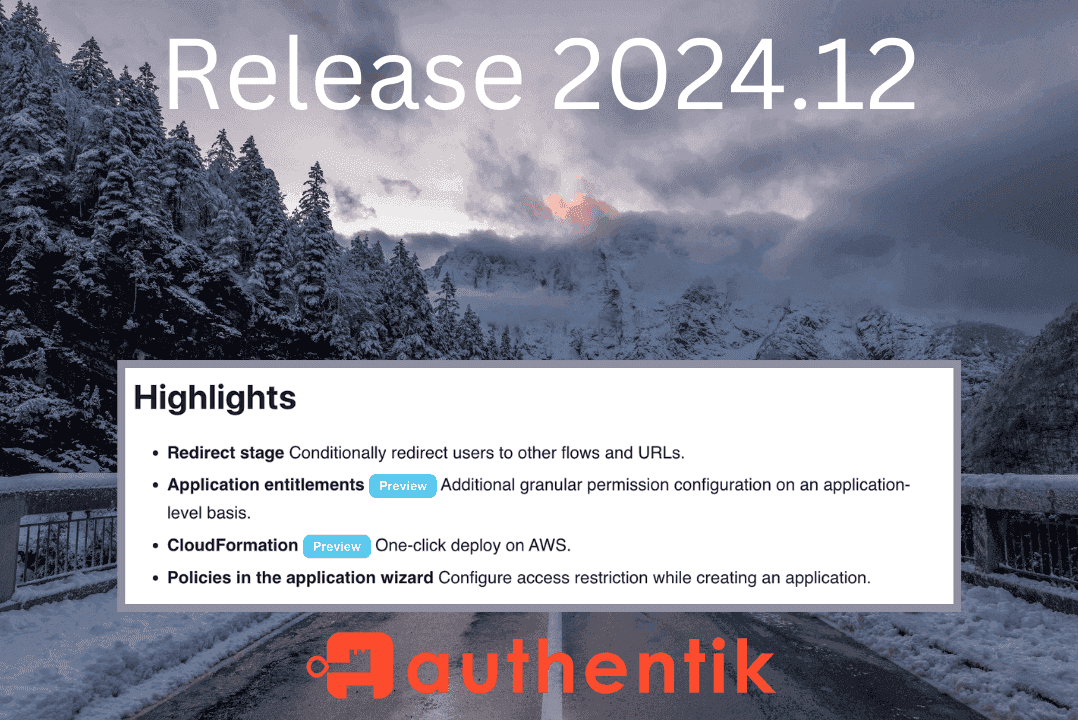
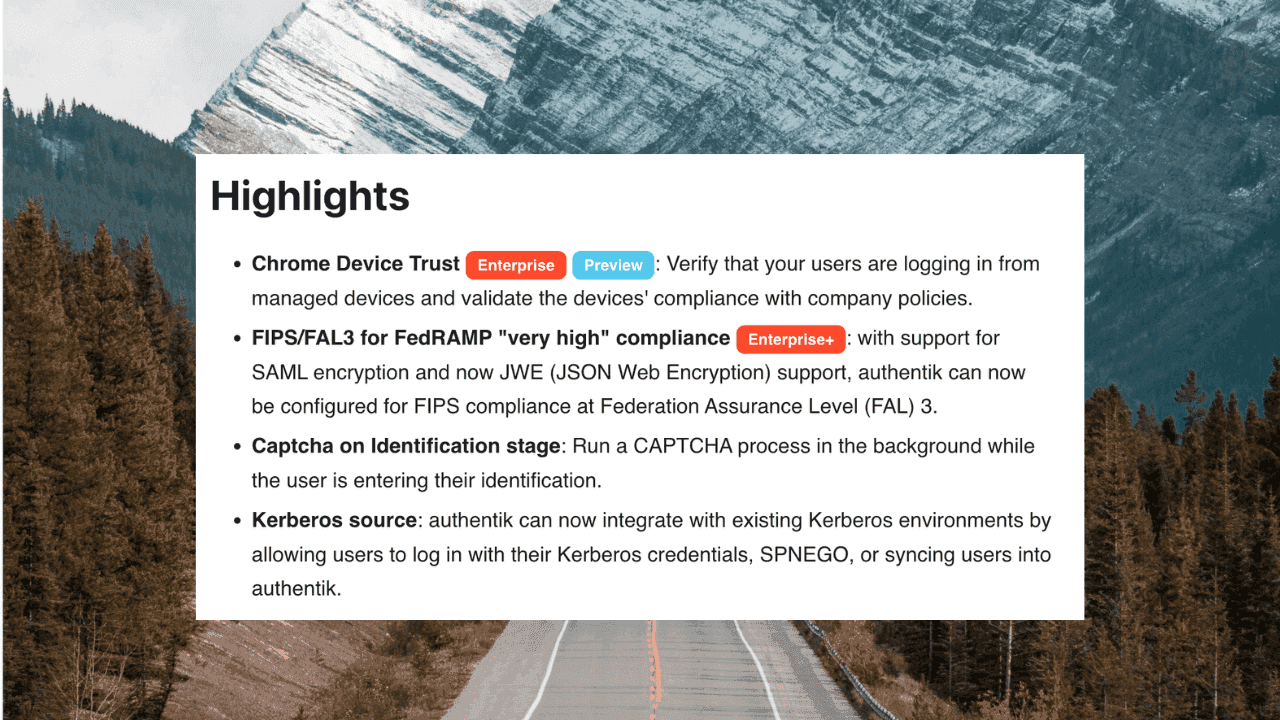
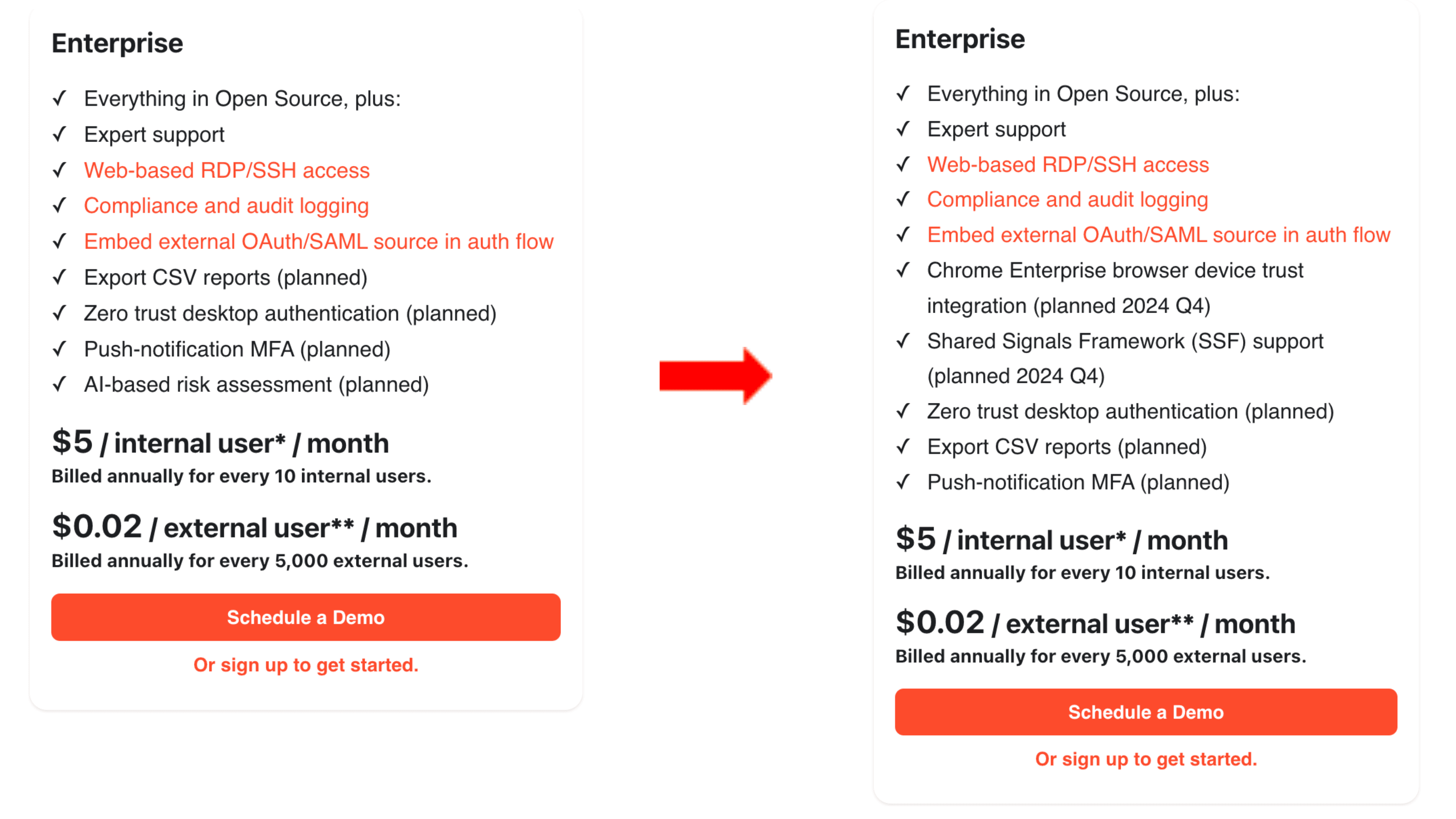
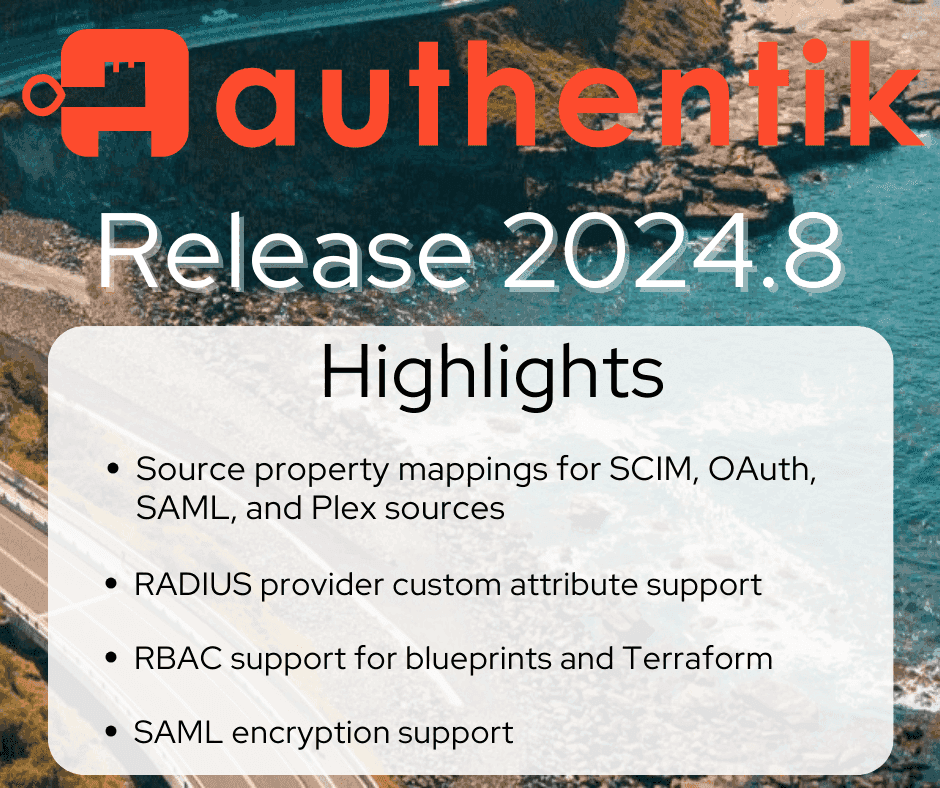
How to break up with your IdP: migrating to a new identity provider
The reason your identity provider (IdP) is so important is the same reason they can be so sticky.
Your IdP touches everything in the business: every user across your entire workforce and all your applications. Setting up access for the right people to the right applications takes time, so it’s natural, when considering moving to a new IdP, to fear an equal time commitment for the migration — not just for configuration, but for coordination and communication across the whole company.
Migrations typically involve a large-scale “Day 0” export of rules and accounts from one provider to another. You flip the switch and hope that everything works after manually setting it all up.
As if switching one IdP isn’t hard enough, it’s not uncommon for companies to have multiple solutions stitched together. Individual teams may have come up with their own solutions, or they could have inherited systems from acquisitions or organizational changes. This leads to scenarios where large organizations might even have three or four different IdPs, directories, or other solutions patched together. Each of these might be on its own contract renewal cycle, making it difficult to coordinate a switchover without incurring a cost.
On the one hand, migrating IdPs is intimidating and risky. On the other, you face the administrative cost of maintaining a host of separate identity solutions, plus the security risk of not having a single place for visibility or administration of access.